Slack integration with HyperSign SSO using SAML 2.0
By Dev Gurung on 2020-06-15
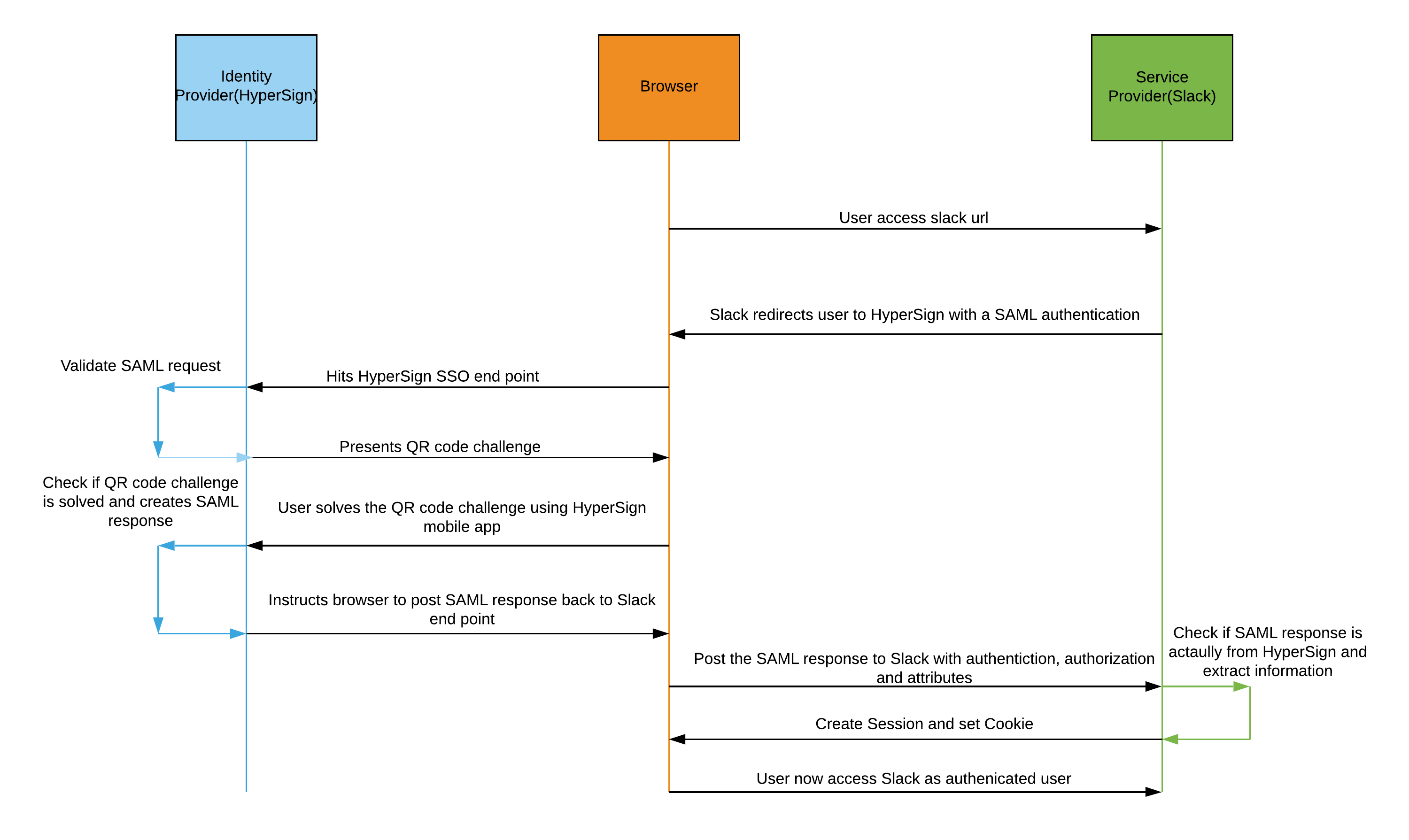
In this blog, we are going to see how we can Integrate Slack(Service Provider) with HyperSign SSO(Password-less Identity provider) using a custom SAML 2.0 configuration. Before we see what exactly we need to do to integrate Slack with HyperSign SSO, let’s see what SAML2.O is all about. SAML2.0 Security Assertion Markup Language (SAML) is an open standard that allows identity providers (in this case its HyperSign) to pass authorization credentials to service providers (like Slack, office 365, salesforce, etc), and with that, using single Identity provider, a user can log in to multiple websites without having to maintain multiple credentials.
In depth introduction to Self Sovereign Identity (SSI)
By Vishwas Anand , Likitha Soorea on 2020-06-14
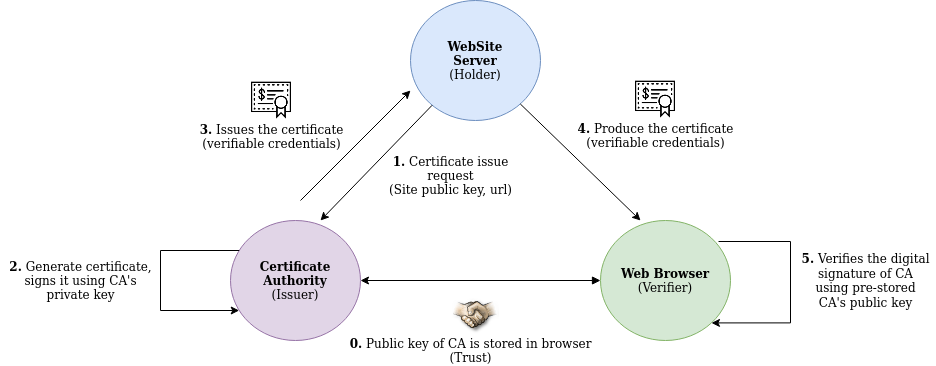
In our previous blog titles - Digital Identity: Past, Present and Future, we went through the journey of digital identity and tried understanding how it evolved over the period and where it is heading. We ended our discussion with the basic introduction of Self Sovereign Identity (SSI) system. If you have not read that blog, I encourage you to read that first before proceeding with this blog. In this blog, we will take a deeper dive into SSI and will try understanding how it works under the hood.
#SSI #digital identity #DID #authentication #centralised #federated #user-centric
Digital Identity: Past; Present; Future
By Vishwas Anand , Likitha Soorea on 2020-04-19
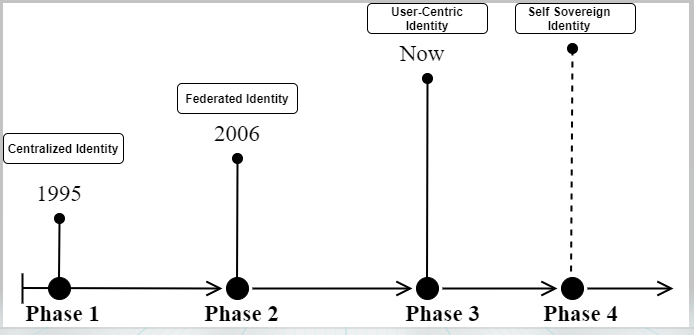
Today, many countries across the globe are implementing digital identities to accelerate the adoption of their digital services. While going through the research articles on digital identities, one of the questions raised is “why is the digital industry looking up for it?”. We’d like to share some experiences on this journey, let’s start with a basic question “what is an identity?” take a moment to think… and try to put the thoughts into a clear definition.
#SSI #digital identity #DID #authentication #centralised #federated #user-centric
Trustless - The third vertical of credentials management
By Vishwas Anand on 2020-03-14
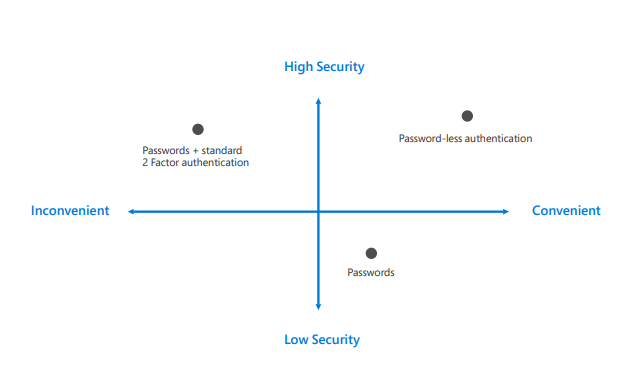
Identity management (IM) has always been a challenge for companies, whether it’s securing their internal employee’s access to company systems and applications, or securing their customers to access the web apps and databases. This aspect has two major components, Management of identity and Management by identity. Management of identity is primarily Authentication and Management by identity is Authorization. Traditionally, common methods of managing digital identities such as usernames and passwords have been proven to be less secure.
#trust #trustless #fido #authentication #passwordless #public-key-infrastructure #cryptography
A quick introduction of Biometrics
By Vishwas Anand on 2020-03-14
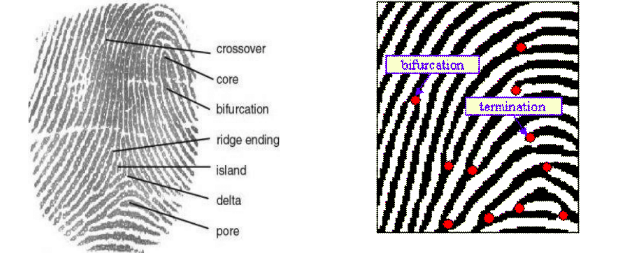
In this blog, our purpose is to take an in-depth look at how biometrics works. There are multiple types of Biometrics like Facial characteristics, Fingerprints, Iris pattern etc. and they are fairly complex to understand. So we will just focus on Fingerprints, to make biometric identification process simple and easy to understand. We will start with the definition of Biometric and its types. Then will talk about how fingerprint works, where we will talk about different stages of fingerprint verification process.